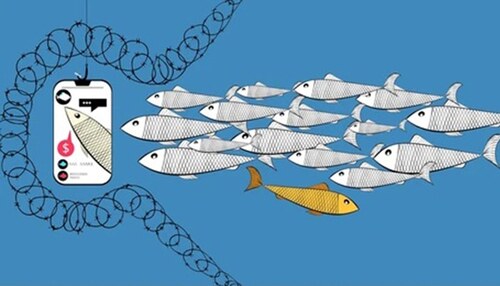
Take 10 minutes away from your busy scrolling of Facebook and search for groups which offer citizens’ personal details — claimed to be from files maintained by the National Database Registration Authority (Nadra) as well as by telecom companies.
You’ll find dozens of these groups.
One group, for example, offers Nadra data which includes “family trees” with pictures for an undisclosed amount of money. Another can provide you lists sorted by cities. And some can go as far as to tag you in your national and provincial constituencies.
Upon exploring two of these groups in more depth — one with over 250 members and one with around 400 members — Eos discovered people offering subscriber details of numbers from various mobile networks in Pakistan, call history and location.
If your cell number is getting unsolicited messages and requests, beware: your personal details have been compromised and your digital imprint is now being tracked.
We got in touch with an administrator of one such group, pretending to be a client, and confirmed if indeed he was selling Nadra data. He replied with, “All types of data [are] available.” This man’s Facebook profile picture was a collage of a family tree of a citizen, Nadra form details, and the photo of a person.
We got in touch with another agent on Facebook, and upon their insistence, contacted them on Whatsapp.
Interestingly, the contact was using a Whatsapp Business account; an automated message listed their company’s various offerings. These included: “locations of all networks, Nadra number details, CNIC pictures, call detail record (CDR), IMEI scanning, fake call, bank account details and secure active sims available.”
We then asked if we can be furnished with a family tree of a person if we provided CNIC details. The gent replied that a family tree with pictures would cost 1,200 rupees and one without pictures would cost 600 rupees.
As Pakistanis’ digital footprint grows, so do the threats to their confidential details. Without data protection laws in place, businesses and criminals are able to misuse private data they should not even have access to
We enquired if he could provide the call history of a particular number. He replied that the rates depended on the cell phone network —3 ,000 rupees for one network and 2,600 rupees for another different network, with data to be provided “within two hours.”
When asked if we could trust him to provide real data and not fake, he said: “See, we provide screenshots from a computer of Nadra data and not handwritten notes. Call history [selling] is also something we have been doing since long, it’s a daily thing for us.” He assured us that data for a particular network would be provided within two hours. Further details were contingent upon providing him with a CNIC number and payment, which we didn’t proceed with.
The buying and selling of personal data has been increasing as Pakistan’s population on the internet increases by the day. An investigative officer with the Federal Investigation Agency (FIA) said that they are aware such groups might exist but said no complaint has been registered by Nadra as yet.
But as internet and telecom penetration in Pakistan has increased, calls for legislation to protect personal data of the country’s citizens have also grown louder.
But what does personal data constitute? Why do we need laws to govern how it is used, retained, shared or processed?
UNDERSTANDING DIGITAL IMPRINTS
There was a time when linking to a national identity card and a passport were the most popular and accessible means to have private data stored in one place. And as Nadra came into being, much of this, as well as data on child registration certificates or family registration certificates was computerised and added to a central storage.
But over time, data has become the new oil — companies little and large are after personal and private details of consumers in an attempt to target their marketing campaigns better to their prospective customers.
While large advertising hoardings were the way of the past, habits and behaviours on Facebook or WhatsApp, for example, are more important to companies now than ever before.
According to Privacy International, any data which can be used to identify an individual directly or indirectly can be termed personal data. A more comprehensive definition is that provided by the European Union’s General Data Protection Regulation (GDPR), which came into effect in April 2016.
The GDPR’s ‘personal data’ definition incorporates “any information relating to an identifiable person who can be directly or indirectly identified in particular by reference to an identifier.” Personal data subjects are identifiable if they can be directly or indirectly identified, especially by reference to an identifier such as a name, an identification number, location data, an online identifier or one of several special characteristics, which expresses the physical, physiological, genetic, mental, commercial, cultural or social identity of these natural persons. For example, the telephone, credit card or personnel number of a person, account data, number plate, appearance, customer number or address are all personal data.
As digital transformations take over governmental processes, almost each and every one of us has a digital footprint — whether we notice it or not. Take, for example, the information entered into your Android phone. These details include your name, telephone number, addresses, etc. In a way, we voluntarily hand over personal data with some degree of confidence that our details will not be used or abused.
But things always don’t pan out that way.
Asad is a low-grade employee at a hospital in Karachi. One day, he was approached by the FIA who told him that a transaction of a significant amount of money has been detected from his account.
Asad was flabbergasted — never could he have dreamt of seeing so much money let alone count it. He didn’t even understand much of how online transactions such as bank transfers or bill payments could be carried out.
He later told investigators that a nurse had asked for his bank details, saying that she needed it for receiving money from a relative and that she did not have her own bank account. Asad had no reason to have any doubts and he handed his bank details over to her.
By the time the FIA approached Asad, the nurse had already made good on her escape.
OFFLINE REPERCUSSIONS
Have you ever switched on your phone to a barrage of unwanted text messages from companies that you don’t care for much? Or have you ever had a request from “Ayesha” or “Sana” to send her some mobile credit? Or better yet, have you ever been informed that you are eligible for the Benazir Income Support Programme?
These text messages are not just irritants; they are meant for you to reply and to comply with directives. Scammers then use your personal information for their gain.
When Shahida ordered a package from a well-known local online marketplace, she didn’t know she would end up being harassed and threatened by unknown men on the phone. She had added her mobile number at the site as it is a requirement to proceed with the order.
Shortly after the package was delivered to her, she started getting calls and messages quoting her address. People from a couple of numbers threatened her to answer their call or they would “show up” at her home. She complained to the company, who were polite and promised to handle the matter, but the messages didn’t stop.
Shahida’s personal data was likely procured from businesses set up to sell this service.
Omer Alvi of Al-Rahim Printers, a small company providing various services, including SMS marketing, boasts of various clients who come for SMS marketing. He says even huge brands utilise SMS marketing to reach out to a large number of people with minimum cost.
“[We] acquire and amass mobile numbers from various sources, such as the Yellow Pages, phone directories, business cards, and door-to-door surveying, where they ask residents for their contact details,” he explains. “It takes hard work. I also purchase lists from other SMS marketing companies from Karachi and, rarely, from Lahore too. I pay 150,000 rupees to buy a list from a Karachi-based company.”
The old method for spammers was to take one number and change the last digit and generate a series. Another technique was to scourge Facebook, Twitter and LinkedIn for mobile numbers, which the users may have kept on public view.
Alvi says he is looking to now sell SMS marketing software, which is in high demand, especially to housing societies and travel agencies who are looking to do it themselves rather than outsource. Al-Rahim Printers charges 1,500 rupees for 10,000 messages and 3,500 rupees for 50,000 messages.
“That is how cheap your mobile number is up for — the digits which are linked to your bank account, your social media accounts, your email and your ride-hailing app,” he says. With these digits on hand, they can be misused in more ways than fathomable.
Al-Rahim Printers charges 1,500 rupees for 10,000 messages and 3,500 rupees for 50,000 messages. “That is how cheap your mobile number is up for— the digits which are linked to your bank account, your social media accounts, your email and your ride-hailing app,” he says.
Such fraud is becoming increasingly commonplace but, slowly, it is beginning to claim droves of victims rather than just individuals.
Popular ride-hailing company Careem warned its customers on April 23 last year that a massive data breach had compromised their data, including name, ride history and email addresses. Users’ passwords and credit card details were not stolen, the company reassured clients. No details about the nature of the cybersecurity attack were given and the company was not answerable or liable in the absence of a data protection law in Pakistan.
But the bigger moment of reckoning arrived in November last year when the FIA announced that the data of millions of customers from “almost all” banks operating in the country was stolen and allegedly dumped on the ‘dark web’ — a collection of websites that exist on an encrypted network and cannot be found by using traditional search engines or visited by using traditional browsers. It was the biggest data breach to hit the banking industry in the country. According to the FIA, an international company named Group-IB, which was working in Pakistan to prevent cyberattacks, had discovered the payment details of 177,878 plastic cards from Pakistani and other international banks.
The banks affected by this breach included Habib Bank, MCB, Allied Bank Limited, and many others. Habib Bank was the most affected by the breach. Around 150,000 dumps of data of Pakistani banks went on sale on the dark web. The company reported that another data dump of around 70,000 Pakistani banks cards’ data with PINs — Personal Identification Numbers — was on sale for 50 dollars in January.
What is common between all these instances is that none of the companies or organisations that had data leaks had to face any repercussions or even tough questions about putting sensitive user data at risk. There remains a lot of obscurity about whether proper mechanisms are in place to prevent such incidents in the future and, for that matter, details about the nature of attacks and what is done to address them.
In the absence of any legislation on data protection, a common citizen has no way to legally ask questions from the government departments and private companies as to how and why their data is being held, retained, processed and shared.
THE POLITICS OF PRIVACY

A month before the general election in July last year, the Pakistan Tehreek-i-Insaf (PTI), which was in opposition then, accused the Election Commission of Pakistan (ECP) of sharing voters’ data with the Pakistan Muslim League-Nawaz (PML-N).
The ECP was accused of sharing sensitive data with PML-N to help it “influence” the election, after a list of electoral rolls was published by a media house. Before that, in May, various news reports suggested that sensitive data of citizens had been exposed to hackers through a software of the Pakistan Information Technology Board (PITB), which was then allegedly sold on various groups on Facebook and other social media.
Fingers were inevitably pointed at Nadra, which has been at the centre of controversy multiple times surrounding the handling of sensitive data. Nadra rebutted all allegations, but experts reiterate that reports of breaches show an absence of proper mechanism to secure and handle data.
Shehryar Hyderi, General Secretary of the Pakistan Software Houses Association (P@SHA), argues that a lot of leaks of entire lists of mobile numbers from telecom companies were reported to have been carried out by individuals who either worked for these companies or had worked for them at some point in time. An investigative officer with the FIA agrees that it is mostly likely the employees behind leaking lists of cell phone numbers. When asked about whether law enforcement went after such individuals, the officer claimed that no complaints were ever launched because no cellular company or individual approached them.
Nadra employees have faced the same allegations, although Hyderi says stealing the data from the authority’s portals is surely not easy. “You would have to screenshot and then export that file. It won’t be that easy considering Nadra most certainly has anti-data theft mechanisms in place.”
The first real debate about privacy and data protection after the telco and digital boom in Pakistan started in 2012, when the Pakistan Telecommunication Authority (PTA) ordered telecom companies to terminate late-night call packages and reportedly used transcripts of a private phone conversation between two people as the justification for its decision in court.
Civil society and even individuals meted out severe criticism to the authority, which is responsible for the establishment, operation and maintenance of telecommunications in Pakistan. Experts questioned if the PTA had any authority to intercept private phone calls between common citizens, much less present them in court as evidence.
Seven years down the line, much has changed.
Today, there are virtual profiles of each one of us on the internet, accessible to anyone, made using data which we may or may not have agreed to be shared. The ride-hailing app you use can trace out an entire profile of you by looking at the places you frequent. An ad flashes of the product or service on Facebook, soon after you talk about something with your friend. The world’s most valuable resource is data. Attempts to hack and dump this valuable resource have increased more than ever globally.
While some government departments such as Nadra and PITB have data protection clauses in the laws governing these bodies, Pakistan has no all-encompassing legislation that would cover government as well as private companies.
Speaking with Eos, former senator Farhatullah Babar, a vocal advocate of digital rights, says a data protection law is the need of the hour. He says that the Prevention of Electronic Crimes Act (Peca) shouldn’t have been passed in the first place in 2016 without a data protection law in place.
“The [previous] government had promised us that a data protection bill would be tabled within two months after Peca was passed but they never did so,” says Babar. “The incumbent government has also made no headway on the issue and no draft law has been presented before the parliament.”
The law is especially necessary because online clampdowns by the state have seen a significant increase since early 2017, with the incumbent PTI-led government being blamed for taking it to unprecedented levels.
Journalists, activists, and supporters of opposing parties, especially PML-N, have faced threats and intimidation by the FIA. Experts say the FIA routinely uses the cybercrime law to crack down on any kind of dissent against the state and the security apparatus.
In such a scenario, it remains unclear as to what extent authorities have access to a detained individual’s private data, for example, from accessing and taking into custody their electronic devices, and their social media and email accounts. In the absence of a law, citizens remain vulnerable to having their personal and private data used against them, even if there is nothing criminal about it.
UPTICK IN CYBERCRIME
Pakistan has seen a significant uptick in cybercrime, including online abuse, online banking fraud, ATM skimming, impersonation, hacking, etc., in the last decade. According to the FIA, which is authorised to probe and prosecute under the cybercrime law, 587 cases have been registered under Peca and six convictions have been made from September 2016 to December 2018.
Many of these cybercrimes involve accessing a user’s data through some means. Media outlets reported dozens of cases in which fake bank accounts were set up in a person’s name, who was oblivious to this, with money being dumped in the accounts. One case included that of a bank account opened in a dead person’s name.
Last year also saw dozens of unsuspecting bank customers losing their money when cyber criminals duped them into giving their bank account details by impersonating bank employees. As many as 1,244 online banking fraud complaints were received in the first 10 months of 2018, the interior ministry had briefed the Senate in December.
How did the gangs acquire the mobile numbers of ordinary citizens and information about what banks they have opened accounts with? Where did criminals acquire details of a person to open a fake account in his name? Why were accounts being opened in the names of daily wagers, rickshaw drivers, and fruitsellers? Was it intentional as these members of society would likely have been oblivious that their name and details were being used?
In the case of bank accounts, it is mostly the bank employees and the branch manager who are found to be involved, says Muhammad Ali Abro, the deputy director FIA banking in Sindh. And where do they get the details from to open a bank account. “In rural or impoverished areas, people may masquerade as agents providing jobs to the needy. People desperate for jobs often give their details to them, and get duped into opening bank accounts. These accounts are then used for money laundering,” he says, adding that “influential people” can also pressure a bank manager to open fake accounts.
Meanwhile, an investigative officer (IO) with the FIA in Karachi confirms that no citizen or consumer has ever approached them for complaints regarding unnecessary holding or processing of their personal data. It is only after a crime is committed that people begin approaching the agency.
Almost exclusively, online marketing and companies providing some sort of consultancy services have, however, approached the FIA for stealing of their data.
The IO says that between eight and 10 complaints were brought before them in 2018. These mostly included employees stealing their former companies’ data, such as the source code of the companies’ internal portal where data was stored or client data, and sharing it with the new one. But these were mostly settled out of court as companies did not want to get into lengthy court battles and lose more money.
The complaints were launched under sections 420 and 419 of the Pakistan Penal Code, meaning charges of fraud, and section 14 of Peca — which pertains to the unauthorised use of identity information — as no legislation exists for data theft.
Then there are other cybercrime categories. Suspects vary from a disgruntled husband sending continuous unsolicited messages to his wife to get her to reconsider getting a divorce, to a woman running false news of the daughter’s engagement about the family of a rival powerful business family, the FIA official explains.
Faizullah Korejo, head of FIA’s cybercrime wing in Sindh, tells Eos that online harassment of women forms a large part of complaints received by them. Most of these comprised of ex-husbands and ex-lovers using private and/or intimate pictures to blackmail the woman.
Due to strict social norms and societal misogyny, many women prefer to settle such complaints out of court; sometimes not even a complaint is registered. This mostly entails the FIA nabbing the accused and forcing him to delete any private or objectionable content stored on their phones, laptops or other such electronic equipment.
An uptick has also been seen in online financial scams, in which many people were duped into giving money by investing in cryptocurrency such as Bitcoin. Other complaints came from citizens who were duped into buying false products on popular online marketplaces, such as OLX, by sellers who would switch their numbers off after the transaction.
Last year, there was a barrage of news about some people who asked people for their bank account details pretending to be Pakistan Army officers. Many people lost their money, and the military’s media wing, the Inter-Services Public Relations, was forced to provide a warning that such people were in no way connected to the army.
The IO at the FIA tells Eos that the callers would often tell the people they called that their money had been used in a certain terrorist activity and that they intended to investigate, for which they required their bank details, including ATM and PIN numbers. This would scare the call receivers who would give up the information. The suspects would then quickly transfer money to one or multiple accounts, or transfer through EasyPaisa. The suspects would also, in most cases, close the accounts used to receive the money. The IO adds that the calls almost exclusively were made in Punjab and the group was eventually nabbed too.
Despite several written requests to the FIA headquarters to provide details on the nature and breakdown of cases of cybercrime, no details were given. An official, however, confirmed that no complaint till date has been filed specifically for theft or misuse of data, but that incidents such as telephone banking fraud were being investigated under various other cybercrime acts of Peca.
A senior official in FIA concedes that such type of data on cybercrimes might not be available at all. “This is what you can call research,” he says, “but unfortunately we are not even close to proper investigation and closing of cases which are already open. I don’t think we have enough manpower or resources to maintain a comprehensive data of numbers and the nature of crimes.”
In January, some images of couples in an intimate position went viral on social media. The images were allegedly taken from one of the closed circuit television cameras (CCTVs) installed at various locations in Punjab and Islamabad under the ‘Safe City’ projects.
The alleged leak stirred up once again the debate on there being a lack of transparency in the data collection, usage and retention of data in these projects, and whether robust mechanisms are in place to protect that data, especially, personal and up-close pictures of individuals.
Till now, the only prognosis is that officials are still struggling to come to terms with how technology is being misused and abused. The danger in Pakistan, due to the absence of laws and regulations, is that law enforcement routinely crosses the line between surveillance and safety, although they are not one thing. And in such situations, common citizens shall always be vulnerable.
The writer is a freelance journalist based in Karachi. She tweets @Sindhu_Abasi
Published in Dawn, EOS, June 2nd, 2019