When it comes to cyberspace, most users will believe that they have a fairly firm grasp on what the internet has to offer. For such people, the World Wide Web is a source of news, entertainment, communication, commerce, and ahem, ‘nature’ videos.
Of course, there also exist the darker corners of the World Wide Web which are frequented mostly by Death Eaters and Sith Lords — so to speak. Although such websites flirt with the law, they are still accessible by anyone who knows how to use a search engine. Typically, this more accessible portion of the internet is known as the ‘Surface Web’.
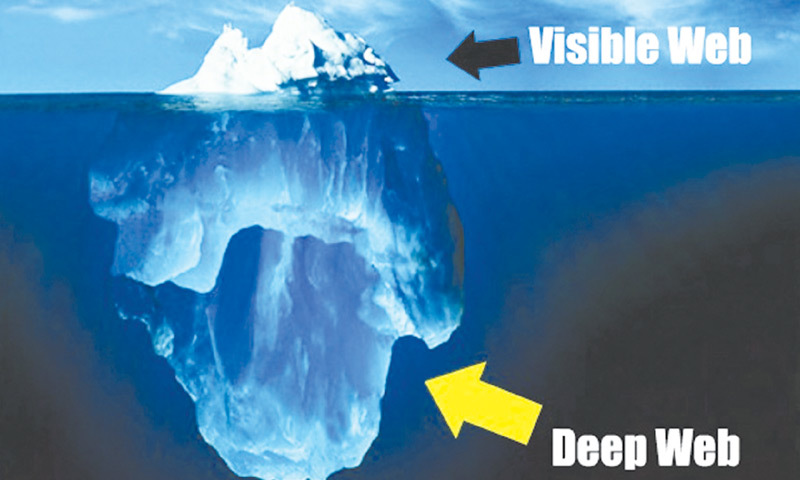
It may come as a surprise to some, but there also exists content on the internet which is inaccessible by regular means. Known as part of the ‘Deep Web’, such websites aren’t indexed by regular search engines and feature a random string of letters as their web address. If you are wondering how deep this rabbit hole goes, well Alice, most experts find it almost impossible to ascertain the exact size of the Deep Web which, similarly to the universe, is in a state of constant expansion. But metaphorically speaking, you can think of the Surface Web as the tip of the iceberg, and the Deep Web as the vast underbelly of the murky beast.
If you go beyond the surface, the ‘real’ internet is a complex parallel world of secrets and anonymity that runs deeper and is bigger than you could’ve ever imagined
 |
Navigating the Deep Web isn’t as difficult as you may think. It is accessed by special software such as Tor (the Onion Router), which can open cryptic web addresses in the Deep Web, allowing its users to browse anonymously. These web addresses can be found on Deep Web directories through popular search engines, while the Tor software itself is a simple download from its official website. What’s more, because the Tor browser uses the Mozilla Firefox software, it is as easy to use as any web browser.
Interestingly enough, the concept for the Tor software took shape in the 1990s by members of the U.S. Naval Research Laboratory. The goal was to create a tool to protect the interests of the United States government so that American intelligence operatives could covertly communicate online. Later, in 1997, the project was developed further by DARPA, an arm of the United States Department of Defense.
 |
After the alpha version of the software was developed, the U.S. Naval Research Laboratory opened the code for Onion Routing for free in 2004. Here, the non-profit digital rights group, Electronic Frontier Foundation (EFF), championed Onion Routing with funding, and eventually the Tor project was backed by companies such as Google, Human Rights Watch, amongst others.
Thanks to the fact that it provides anonymity, the Tor software allows its users many advantages, especially during times of political unrest. Reportedly, Tor has been a vital tool for activists against their government, with one of the most popular examples being that of dissidents in Egypt who used Tor when their internet freedoms were threatened.
Known as part of the ‘Deep Web’, such websites aren’t indexed by regular search engines and feature a random string of letters as their web address. If you are wondering how deep this rabbit hole goes, well Alice, most experts find it almost impossible to ascertain the exact size of the Deep Web which, much like the universe, is in a state of constant expansion. But metaphorically speaking, you can think of the Surface Web as the tip of the iceberg, and the Deep Web as the vast underbelly of the murky beast.
But in what is perhaps embarrassing for the United States government — considering their hand in developing Tor — the most famous user of the Onion Router is Edward Snowden, the former NSA employee who today is known as one of the most famous whistleblowers in the world. For a long period of time Snowden passed on sensitive information to outsiders, and did this undetected using an anonymity software called Tails which utilises the Tor encryption software.
The Tor browser also allows its user to have complete access to websites such as YouTube, Twitter, or Facebook. This is especially useful in countries where such websites are banned completely, though due to the nature of Tor, such websites do perform more slowly.
If you are wondering how Tor works, the secret is in the name. Much like the layers of an onion, Tor offers several levels of protection to protect its users’ privacy. Here, each layer of data is encrypted multiple times through a virtual circuit. With the information being routed through a network of computers, the eventual data is almost impossible to crack.
As can be expected, the effectiveness of Tor has proven to be a double-edged sword. Using the .onion suffix, countless websites have spawned across the Deep Web offering every level of vice imaginable. Here, marketplaces offer everything from weapons, ammunition, drugs, and prostitutes, to more frightening elements such as assassins for hire. Surprisingly, the most popular of these websites are developed as well as e-commerce giants like eBay or Amazon. Not only do these marketplaces feature robust designs, but detailed feedback ratings systems as well (naturally, so that their buyers can find the online smuggler who is right for them).
 |
Of course, sellers at these marketplaces only accept Bitcoin as their method of payment. This makes sense since this peer-to-peer crypto-currency also offers anonymity. Interestingly enough, the rise of Bitcoin’s value has been strongly linked with popularity of the illicit marketplaces on the Deep Web. When the biggest of these marketplaces, the Silk Road, was shut down after the FBI nabbed its owner who went by the username ‘Dread Pirate Roberts’, the US government initially seized 26,000 Bitcoins (currently valued at over $9million). Later, in the criminal proceedings against the Silk Road operator, the FBI alleged that the Silk Road had conducted sales worth $9.5m Bitcoins, which equals over $3.5bn today.
Link: http://www.forbes.com/fdc/welcome_mjx.shtml
While intelligence agencies have found it frustratingly difficult to hack the Tor network, they have certainly managed to use their vast resources to capture some criminals who have relied on the Deep Web to do business. For example, the Dread Pirate Roberts wasn’t caught because of a flaw in Tor, but was arrested due to his carelessness which was tracked by the diligent FBI. Similarly, child pornographers have been punished because of their mistakes, the tenacity of law enforcement agencies, and in certain cases, the work of the hacktivist group, Anonymous.
Published in Dawn, Sunday Magazine, November 9th, 2014